Exercise 3: Use the native platform network stack
In this final exercise, we will modify the bookshelf client to use the native platform's networking stack to improve the performance of the network activity and allow us to integrate tighter to the platform. You can either continue from the prior exercise, or use the completed project from the prior exercise if you'd like to start fresh.
To complete the exercise, you will need Visual Studio for Windows or macOS with the Xamarin development tools installed. You will also need either an emulator/simulator or a device to run the exercise on. Please see the setup page if you need help installing the Xamarin development environment.
Techniques for using a native handler
We will modify the iOS and Android projects to use the proper HTTP message handler. There are two ways we could do this:
- We could pass in the platform-specific message handler into the
HttpClientconstructor for iOS and Android. Since we are using a PCL to create the client, we'd have to pass (inject) in the proper implementation from each of our platform head projects. - We can use the IDE switch in iOS and an environment variable in Android to set the default message handler - by default it uses the Mono networking stack, but we can change the default handler supplied to the default
HttpClientconstructor to alter this behavior.
Feel free to experiment with both approaches. The provided instructions use technique #2.
Install a native handler in iOS
Here we will specify the native HTTP handler we would like HttpClient to use in iOS.
- Open the project properties for BookClient.iOS.
- Go to the iOS Build properties.
- Select the Advanced tab.
- Change the HttpClient implementation to be NSUrlSession (iOS 7+).
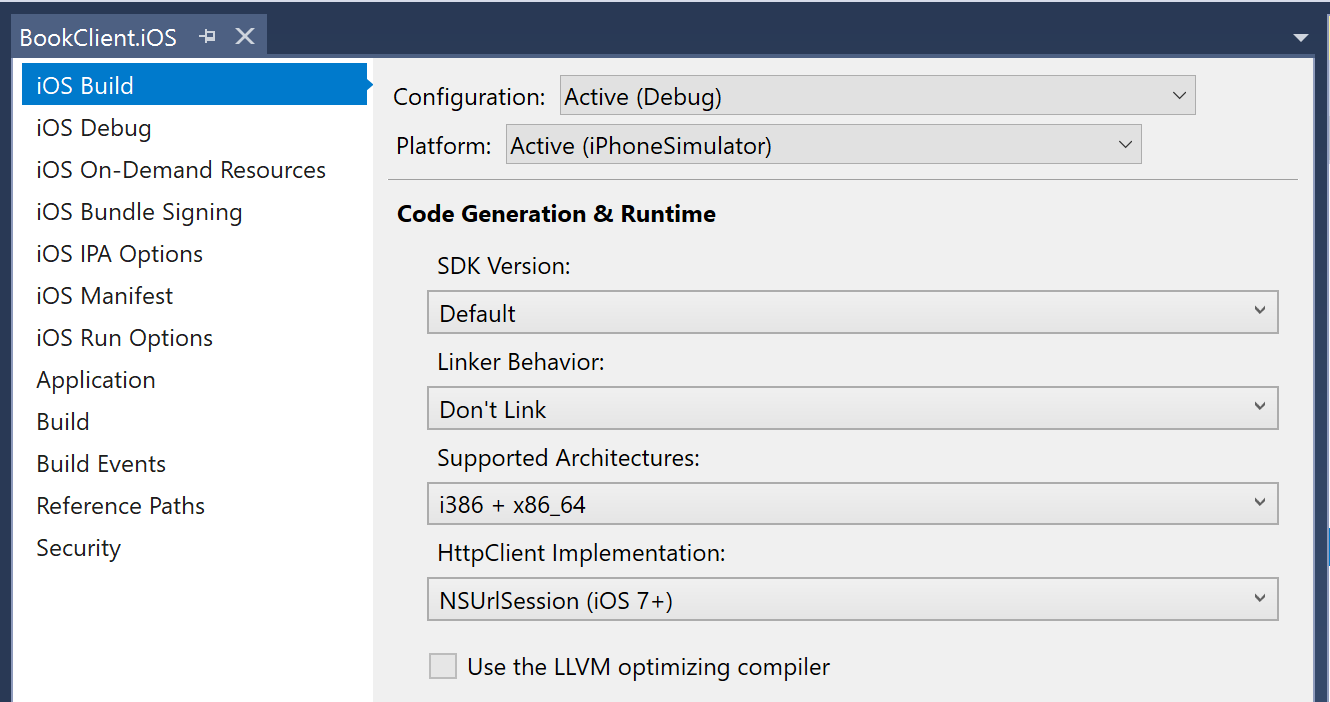
- Run the application. The iOS project might now throw an exception because we are using an untrusted/insecure endpoint. This will only happen if you happen to be using iOS9 or later. We could fix this by switching to an HTTPS endpoint, or by adding an ATS exclusion.
- Change the HttpClient implementation to be NSUrlSession (iOS 7+).
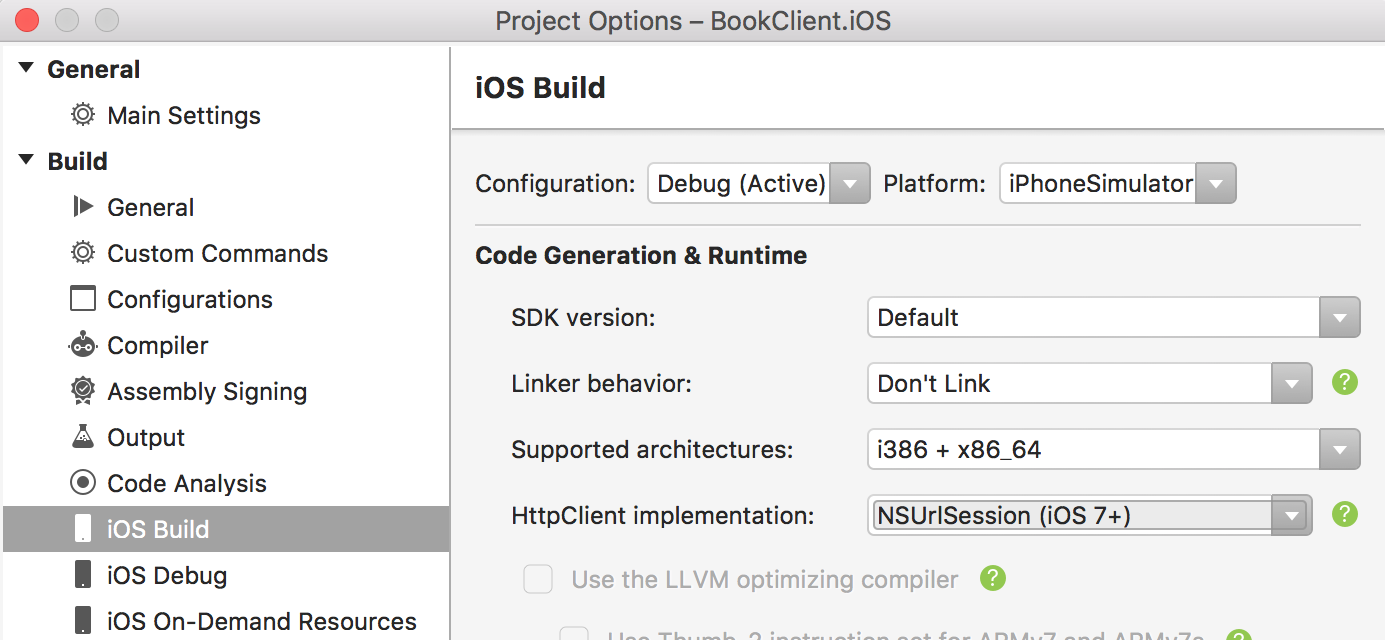
- Run the application. The iOS project might now throw an exception because we are using an untrusted/insecure endpoint. This will only happen if you happen to be using iOS9 or later. We could fix this by switching to an HTTPS endpoint, or by adding an ATS exclusion.
Install a native handler in Android
Here we will specify the native HTTP handler we would like HttpClient to use in Android.
- Open the BookClient.Droid project Properties and switch to the Android Options tab.
- Within the Advanced settings, find the HttpClient implementation drop-down selector.
- Change from Default to AndroidClientHandler.
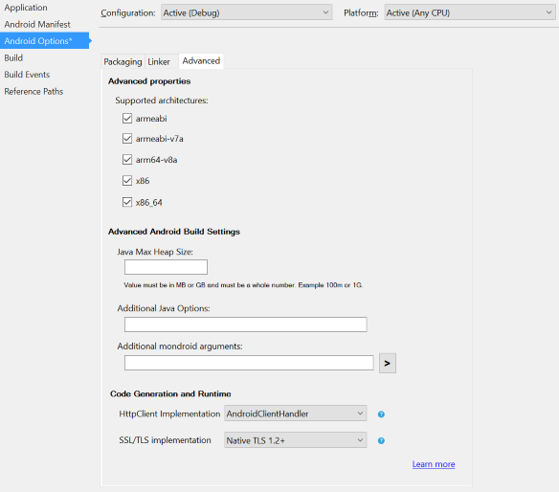
- Open the BookClient.Droid project Options and switch to the Android Options tab.
- Within the General settings, find the HttpClient implementation drop-down selector.
- Change from Default to AndroidClientHandler.
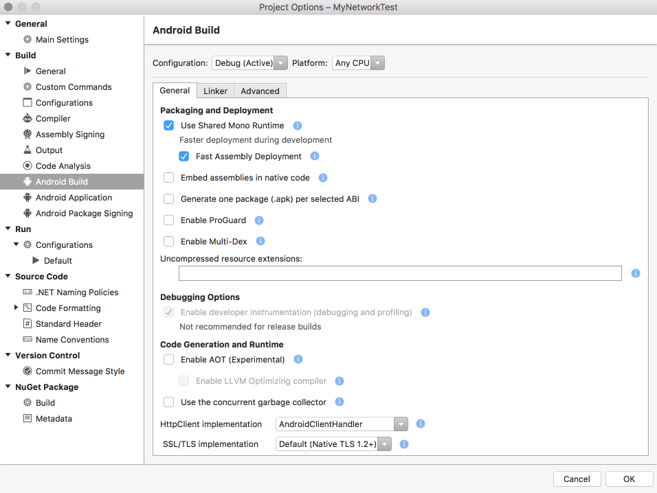
- Run the application. The Android project should run just as it did before.
App transport security policy in iOS
In this final step, we will add keys into the info.plist for our iOS host application to allow the app to communicate with the book server even though it's not using TLS.
- Using an XML editor, open the info.plist file in the BookClient.iOS project. You can also use the GUI editor, but because this key is new, it may be difficult to add it in as a custom key until support is in the GUI.
- At the end of the XML file, just before the final
</dict>, add a<key>forNSAppTransportSecuritywith a child<dict>section. - Fill it with the following code to setup the exclusion for <xam150.azurewebsites.net>.
...
<key>UILaunchStoryboardName</key>
<string>LaunchScreen</string>
<key>CFBundleShortVersionString</key>
<string>1.0</string>
<key>NSAppTransportSecurity</key>
<dict>
<key>NSExceptionDomains</key>
<dict>
<key>xam150.azurewebsites.net</key>
<dict>
<key>NSExceptionMinimumTLSVersion</key>
<string>TLSv1.0</string>
<key>NSExceptionRequiresForwardSecrecy</key>
<false/>
<key>NSExceptionAllowsInsecureHTTPLoads</key>
<true/>
<key>NSIncludesSubdomains</key>
<true/>
</dict>
</dict>
</dict>
</dict>
</plist>
- Run the application a final time and verify that it is now capable of pulling data for the iOS app.
Exercise summary
We are now using an optimized, platform-specific web client implementation to access our REST based services.
You can view the completed solution in the Exercise 3 > Completed folder of your copy of the cloned or downloaded course materials.